Data Center Security: Physical and Digital Layers of Protection
Data is a commodity that requires an active data center security strategy to manage it properly. A single breach in the system will cause havoc for a company and has long-term effects.
Are your critical workloads isolated from outside cyber security threats? That’s the first guarantee you’ll want to know if your company uses (or plans to use) hosted services.
Breaches into trusted data centers tend to happen more often. The public notices when news breaks about APT attacks (Advanced Persistent Threat) succeeding.
To stop this trend, service providers need to adopt a Zero Trust Model. From the physical structure to the networked racks, each component is designed with this in mind.
Zero Trust Architecture
The Zero Trust Model treats every transaction, movement, or iteration of data as suspicious. It’s one of the latest intrusion detection methods.
The system tracks network behavior, and data flows from a command center in real time. It checks anyone extracting data from the system and alerts staff or revokes rights from accounts an anomaly is detected.
Security Layers and Redundancies of Data Centers
Keeping your data safe requires security controls, and system checks built layer by layer into the structure of a data center. From the physical building itself, the software systems, and the personnel involved in daily tasks.
You can separate the layers into a physical or digital.

Data Center Physical Security Standards
Location
Assessing whether a data center is secure starts with the location.
A trusted Data Center’s design will take into account:
- Geological activity in the region
- High-risk industries in the area
- Any risk of flooding
- Other risks of force majeure
You can prevent some of the risks listed above by having barriers or extra redundancies in the physical design. Due to the harmful effects, these events would have on the operations of the data center; it’s best to avoid them altogether.
The Buildings, Structures, and Data Center Support Systems
The design of the structures that make up the data center needs to reduce any access control risks. The fencing around the perimeter, the thickness, and material of the building’s walls, and the number of entrances it has. All these affect the security of the data center.
Some key factors will also include:
- Server cabinets fitted with a lock.
- Buildings need more than one supplier for both telecom services and electricity.
- Extra power backup systems like UPS and generators are critical infrastructure.
- The use of mantraps. This involves having an airlock between two separate doors, with authentication required for both doors
- Take into account future expansion within the same boundary
- Separate support systems from the white spaces allow authorized staff members to perform their tasks. It also stops maintenance and service technicians from gaining unsupervised entry.
Physical Access Control
Controlling the movement of visitors and staff around the data center is crucial. If you have biometric scanners on all doors – and log who had access to what and when – it’ll help to investigate any potential breach in the future.
Fire escapes and evacuation routes should only allow people to exit the building. There should not be any outdoor handles, preventing re-entry. Opening any safety door should sound an alarm.
All vehicle entry points should use reinforced bollards to guard against vehicular attacks.
Secure All Endpoints
Any device, be it a server, tablet, smartphone or a laptop connected to a data center network is an endpoint.
Data centers give out rack and cage space to clients whose security standards may be dubious. If the customer doesn’t secure the server correctly, the entire data center might be at risk. Attackers are going to try to take advantage of unsecured devices connected to the internet.
For example, most customers want remote access to the power distribution unit (PDU), so they could remotely reboot their servers. Security is a significant concern in such use cases. It is up to facility providers to be aware of and secure all devices connected to the internet.
Maintain Video and Entry Logs
All logs, including video surveillance footage and entry logs, should be kept on file for a minimum of three months. Some breaches are identified when it is already too late, but records help identify vulnerable systems and entry points.
Document Security Procedures
Having strict, well-defined and documented procedures is of paramount importance. Something as simple as a regular delivery needs to well planned to its core details. Do not leave anything open for interpretation.
Run Regular Security Audits
Audits may range from daily security checkups, and physical walkthroughs to quarterly PCI and SOC audits.
Physical audits are necessary to validate that the actual conditions conform to reported data.
Digital Layers of Security in a Data Center
As well as all the physical controls, software, and networks make up the rest of the security and access models for a trusted data center.
There are layers of digital protection that aim to prevent security threats from gaining access.
Intrusion Detection and Prevention Systems
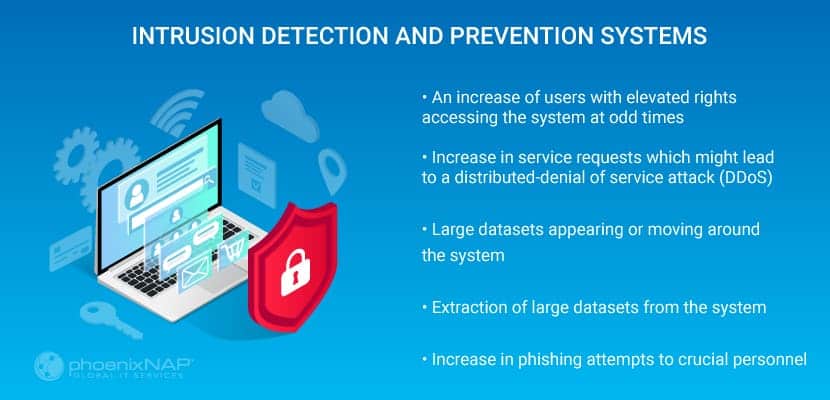
This system checks for advanced persistent threats (APT). It focuses on finding those that have succeeded in gaining access to the data center. APTs are typically sponsored attacks, and the hackers will have a specific goal in mind for the data they have collected.
Detecting this kind of attack requires real-time monitoring of the network and system activity for any unusual events.
Unusual events could include:
- An increase of users with elevated rights accessing the system at odd times
- Increase in service requests which might lead to a distributed-denial of service attack (DDoS)
- Large datasets appearing or moving around the system.
- Extraction of large datasets from the system
- Increase in phishing attempts to crucial personnel
To deal with this kind of attack, intrusion detection and prevention systems (IDPS) use baselines of normal system states. Any abnormal activity gets a response. IDP now uses artificial neural networks or machine learning technologies to find these activities.
Security Best Practices for Building Management Systems
Building management systems (BMS) have grown in line with other data center technologies. They can now manage every facet of a building’s systems. That includes access control, airflow, fire alarm systems, and ambient temperature.
A modern BMS comes equipped with many connected devices. They send data or receive instructions from a decentralized control system. The devices themselves may be a risk, as well as the networks they use. Anything that has an IP address is hackable.
Secure Building Management Systems
Security professionals know that the easiest way to take a data center off the map is by attacking its building management systems.
Manufacturers may not have security in mind when designing these devices, so patches are necessary. Something as insignificant as a sprinkler system can destroy hundreds of servers if set off by a cyber-attack.
Segment the System
Segmenting the building management systems from the main network is no longer optional. What’s more, even with such precautionary measures, attackers can find a way to breach the primary data network.
During the infamous Target data breach, the building management system was on a physically separate network. However, that only slowed down the attackers as they eventually jumped from one network to another.
This leads us to another critical point – monitor lateral movement.
Lateral Movement
Lateral movement is a set of techniques attackers use to move around devices and networks and gain higher privileges. Once attackers infiltrate a system, they map all devices and apps in an attempt to identify vulnerable components.
If the threat is not detected early on, attackers may gain privileged access and, ultimately, wreak havoc. Monitoring for lateral movement limits the time data center security threats are active inside the system.
Even with these extra controls, it is still possible that unknown access points can exist within the BMS.
Secure at the Network Level
The increased use of virtualization-based infrastructure has brought about a new level of security challenges. To this end, data centers are adopting a network-level approach to security.
Network-level encryption uses cryptography at the network data transfer layer, which is in charge of connectivity and routing between endpoints. The encryption is active during data transfer, and this type of encryption works independently from any other encryption, making it a standalone solution.
Learn everything you need to know about Virtual Data Centers by visiting our article What is a Virtual Data Center?
Network Segmentation
It is good practice to segment network traffic at the software level. This means classifying all traffic into different segments based on endpoint identity. Each segment is isolated from all others, thus acting as an independent subnet.
Network segmentation simplifies policy enforcement. Furthermore, it contains any potential threats in a single subnet, preventing it from attacking other devices and networks.
Virtual Firewalls
Although the data center will have a physical firewall as part of its security system, it may also have a virtual firewall for its customers. Virtual firewalls watch upstream network activity outside of the data center’s physical network. This helps in finding packet injections early without using essential firewall resources.
Virtual firewalls can be part of a hypervisor or live on their own virtualized machines in a bridged mode.
Traditional Threat Protection Solutions
Well-known threat protection solutions include:
- Virtualized private networks and encrypted communications
- Content, packet, network, spam, and virus filtering
- Traffic or NetFlow analyzers and isolators
Combining these technologies will help make sure that data is safe while remaining accessible to the owners.
Data Center Security Standards

There is a trend in making data services safer and standardizing the security for data centers. In support of this, the Uptime Institute published the Tier Classification System for data centers.
The classification system sets standards for data center’s’ controls that ensure availability. As security can affect the uptime of the system, it forms part of their Tier Classification Standard.
There are four 4 tiers defined by the system. Each tier maps to a business need that depends on what kind of data is being stored and managed.
Tiers 1 & 2
Seen as tactical services, Tier 1 and 2 will only have some of the security features listed in this article. They are low cost IT services and used by companies who do not want real-time access to their data and who won’t suffer financially due to a temporary system failure.
They are mainly used for offsite data storage.
Tiers 3 & 4
These tiers have higher levels of security. They have built-in redundancies that ensure uptime and access. Providing mission critical services for companies who know the cost of damage to a reputation a break in service creates.
These real-time data processing facilities provide the highest standards of security.
Want to work with a state of the art data center? Contact us today
Take Data Center Security Seriously
More and more companies are moving their critical workloads and services to hosted servers and cloud computing infrastructure. Data centers are prime targets for bad actors.
Measuring your service providers against the best practices presented in this article is essential.
Don’t wait for the next major breach to occur before you take action to protect your data. No company wants to be the next Target or Equifax.