Cloud Storage Security: How Secure Is Cloud Storage?
Storing data on a cloud eliminates the need to buy, manage, and maintain in-house storage infrastructure. Despite this convenience, the lack of control over cloud-based data remains a common concern for businesses, even though cloud storage security is typically superior to any on-premises protection.
This article is an intro to cloud storage security and the techniques cloud providers use to protect data. Read on to learn about the different aspects of keeping cloud-based data safe and see how to distinguish top-tier providers from vendors with inadequate storage protection.
What Is Secure Cloud Storage?
Cloud storage is a cloud computing service that enables a company to store data in the cloud instead of on-site data storage. This model offers a convenient way to keep files on a third-party server and provide employees with on-demand access to data from any device.
Common use cases for cloud storage are:
- Data backups.
- Primary file storage (most common in a hybrid and multi-cloud setup).
- Email storage.
- Disaster Recovery as a Service (DRaaS) for responding to unforeseen events.
- File archives.
- Test and development environments for DevOps teams spinning up storage resources.
As cloud-stored data does not reside on an on-prem server, a company using a public cloud must in part rely on the provider to keep data safe. The good news is that a top vendor's data center uses various practices to ensure data remains secure. These measures often include:
- End-to-end data encryption.
- Advanced cybersecurity capabilities.
- Secure authentication protocols and access control mechanisms.
- Features that guarantee high availability.
- Storing data on servers distributed across multiple locations.
- High-end physical device and infrastructure security.
- Advanced cloud monitoring features.
Is data security your top priority? Created together with Intel and VMware, PNAP's Data Security Cloud is a platform that protects data with robust encryption, strict segmentation controls, and advanced threat intelligence.
How Secure Is Cloud Storage?
If you partner with the right provider, your cloud storage will be safer than any on-prem infrastructure. However, not all cloud storage platforms are the same, and some of them are less secure than the provider likes to admit.
The right provider offers many features and frameworks a company cannot easily (or cheaply) deploy on an on-prem setup. These capabilities include:
- Top-tier redundancy: A provider-level data center has top equipment and software redundancy for disaster recovery scenarios.
- Robust physical security: A high-end data center keeps servers in a far more secure facility than an average in-office server room. Typical measures include 24-hour facility surveillance, fingerprint locks, and armed guards.
- Multi-tiered security features: Cloud providers rely on top hardware and software-based firewalls to filter traffic coming into and out of the cloud storage. The use of an intrusion detection system (IDS) is also a standard measure.
- High-end security testing: Cloud providers run regular vulnerability assessments and penetration tests to ensure the storage security levels are up to par with the latest threats.
- Continuous monitoring (CM): CM ensures the security team has real-time visibility into every server and cloud storage in the facility.
While cloud storage security is likely more robust than what you use to protect on-prem devices, the cloud adds complexity to how data is stored. Your team needs to learn to use new tools, adjust security tactics, and set up new measures to ensure data security.
PhoenixNAP's Bare Metal Cloud enables you to set up custom dedicated server deployments with cloud-like ease and agility without having to wait days or weeks.
Cloud Storage Security Challenges
While beneficial, the decision to move data to the cloud means exposing files to new risks. Below is a look at the most common risks and concerns of cloud storage security.
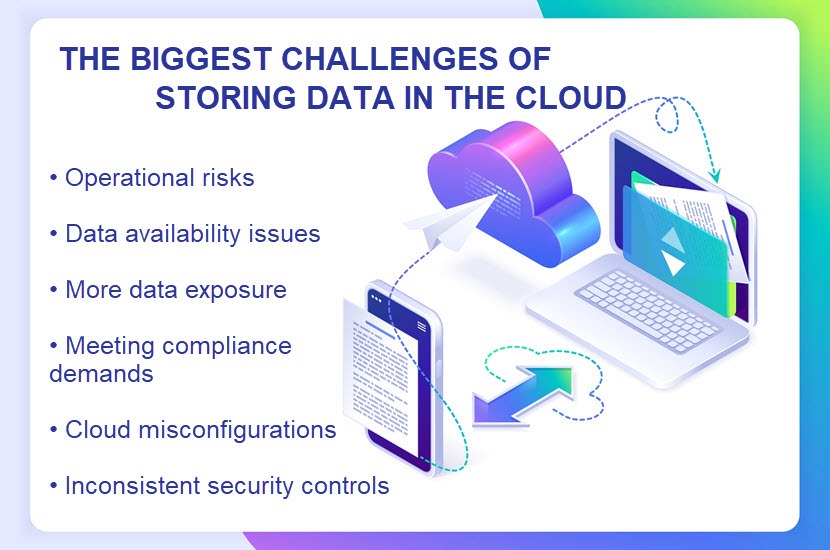
Operational Risks
Nearly all cloud security failures result from an operational mistake made on the client's side. The most common mistakes include:
- Employees using unapproved cloud storage services or platforms without the security or IT team's knowledge.
- Sharing files with the wrong user.
- Accidentally deleting valuable data.
- Losing an encryption key due to poor key management.
- Relying on a weak and easy-to-crack passwords.
- Employees using unapproved and unsecured devices.
The use of unauthorized devices is an especially high risk for a company with a Bring Your Own Device (BYOD) culture. In that case, the management must create and enforce a strict BYOD policy to ensure safe operations.
Check out our post on cloud repatriation. Learn what it is and read about its benefits for data security.
Data Availability Concerns
Operational risks can also occur on the service provider's side. Common issues include:
- Service disruptions due to server failure or a staff member's mistake.
- A local disaster (power outage, fire, earthquake, etc.) that causes hardware failure and downtime.
- A successful cyberattack targeting the provider directly or through another cloud user.
If something affects your storage provider, the event will directly impact access to your data. You must wait for the provider to fix the issue, and the team may not have access to cloud-based data until the vendor's team resolves the problem.
More Data Exposure
A large part of data security is making sure no one outside the team can access the data. When you rely on a partner to store files, you increase the attack surface via which a malicious actor can reach your data.
Even if you take proper precautions to ensure no one in the team leaks data, your storage provider might accidentally expose your files and cause data leakage or pave the way for a costly attack.
Regulatory and Compliance Obligations
Since compliance demands vary based on how and where a business stores data, cloud storage must meet all the relevant requirements. These demands can dictate the way a provider must:
- Store and process data.
- Control access to files.
- Segment the storage.
- Delete data.
- Keep data safe.
Besides meeting current requirements, the cloud service must also be flexible enough to enable a business to adapt to new demands and regulations.
Misconfiguration Issues
Cloud misconfiguration is any error or glitch that exposes cloud data to risk. Since the end users have reduced visibility and control over data and operations, misconfigurations are a common problem.
Cloud storage misconfigurations typically result from:
- Inexperienced engineers.
- IT mistakes.
- Poor resource and operation policies.
A misconfiguration can often lead to a data breach, either from an insider threat or an external actor who gains access to the cloud.
Inconsistent Security Controls
Conflicting and overly complex security controls can also cause issues. The most common problems appear when the provider's and client's teams set up inconsistent rules that leave security gaps a hacker can exploit.
There are two ways to alleviate the risk of conflicting security controls:
- Go with a cloud storage solution that enables your team to set up and manage basic security controls.
- Partner with a reliable provider that agrees to shoulder the entire responsibility of data storage security.
Our article on cybersecurity best practices outlines security measures and tactics that play a vital role both on-premises and in the cloud.
Cloud Storage Security Best Practices
Cloud storage security is a shared responsibility between the service provider and the consumer. If only one side has strong data protection, the lack of security on the other end will lead to risks and attacks. Providers and consumers should approach cloud storage security in the following way:
- The provider should implement baseline frameworks for their platforms (authentication protocols, access control, high-end encryption, etc.).
- Clients should supplement native frameworks with extra measures to bolster security and tighten access to cloud data.
Below is a look at the best practices of cloud storage security that enable vendors and service consumers to ensure data safety.
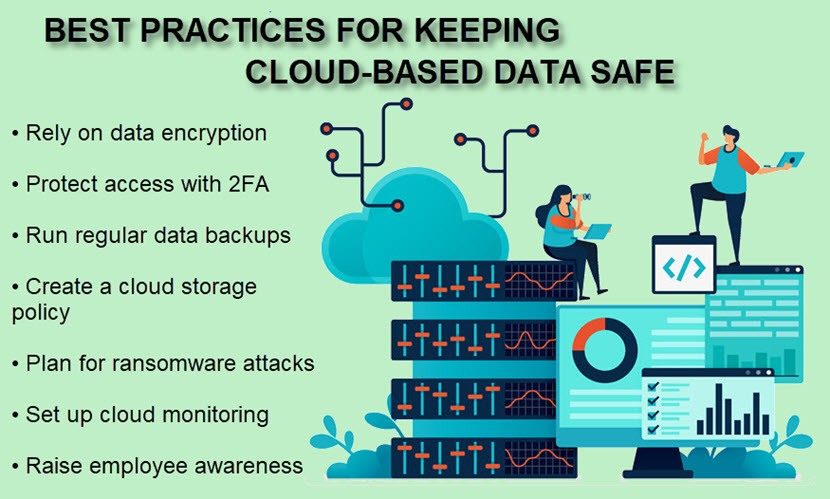
Data Encryption
A cloud provider must encrypt cloud data. That way, if a malicious actor or program accesses a file, all the unauthorized user will find is scrambled data. The only way to decipher data is to use a decryption key.
A provider should encrypt data both at rest and in transit:
- Encryption at rest protects stored cloud data that is not currently in use (AES 256-bit encryption is the most popular option).
- Encryption in transit protects data while files move between two cloud or network points (TLS/SSL 128-bit encryption is the most common choice).
A company can boost cloud storage security with client-side encryption. With this strategy, encryption and decryption happen on the target user's device. There are no encryptions or decryptions on the provider's server as the vendor does not keep any keys. Even if a hacker breaches the provider's server, the thief will not obtain your decryption key.
Regardless of what type of encryption you rely on, you should enforce encryption key management best practices to ensure the team handles keys without adding unnecessary risk to data.
Two-Factor Authentication (2FA)
Two-factor authentication (2FA) requires a user to provide two pieces of info during login. Besides a username and password, 2FA also requires the employee to give an additional credential, which can be:
- A biometric scan (face or finger scans are the most common options).
- A one-time PIN sent to the user's email address or phone.
- A hardware token (typically a USB).
Two-factor authentication adds an extra layer of security that prevents an unauthorized actor from accessing cloud storage with a stolen password (a common target of phishing attacks). Always look for a provider that enables the use of 2FA.
Data Backups (On Both Sides)
Both you and your cloud provider should create regular backups:
- The provider should create regular cloud data backups and spread files across several data centers. If one of the servers goes offline, the client will not suffer downtime.
- You should back up your most sensitive (or all) cloud-based files in an on-prem hard drive. Keep these backups immutable and update them regularly to avoid data loss in any scenario.
PhoenixNAP's cloud backup solutions enable you to set up customizable, immutable backups of all critical data and workloads.
Develop a Cloud Storage Policy
A cloud storage policy ensures your employees understand the company's approach to storing and managing data in the cloud. This document should evolve with your company's current needs and the cloud services the team uses. A policy should provide:
- A clear overview of all cloud-related business objectives.
- Guidelines for when and how employees should use cloud storage.
- A list of best practices when working with cloud data.
- Instructions on what data should go to which cloud storage.
- An overview of all compliance and regulation responsibilities.
- All configuration standards.
If you rely on hybrid cloud architecture, your policy should also cover practices for accessing, managing, integrating, and governing cloud usage within your unique hybrid environment.
Our article on cloud security policies shows how to create a company-wide guideline that dictates how the team operates in the cloud.
Ransomware Protection
A ransomware attack enables a hacker to encrypt your data and demand a ransom in exchange for the decryption key. If the victim refuses to meet the demand, the criminal deletes the key and, as a result, renders target data useless.
This cyberattack type can be devastating to your finances and reputation, so you should always partner with a cloud provider that offers high-end ransomware protection.
PhoenixNAP offers robust ransomware protection that relies on a mix of infrastructure security and immutable backups. To learn more about this threat, check out our article on different ransomware types and our DIY guide to preventing ransomware.
Cloud Storage Monitoring
Continuous change, access, and activity monitoring help identify and remove potential threats to cloud storage. Most storage services include robust cloud monitoring with alerts for:
- New sign-ins.
- Account activity.
- Data shares.
- File deletion.
- Unusual and suspicious activity.
In addition to the provider team's alerts, you can also deploy your own cloud monitoring tool. An extra tool ensures you take a proactive approach to cloud storage security and that your team can identify threats emerging from your end.

Educate Employees About Cloud Storage Security
Educating employees about cloud storage security goes a long way toward protecting files in the cloud. Organize training sessions that familiarize employees with all major aspects of your cloud storage policy, including:
- What data they should store on the cloud, and what files should stay on-prem.
- Safe data-sharing practices.
- Approved cloud storage tools and platforms.
- The risks posed by sharing and storing data on the cloud.
- Relevant configuration standards.
- Internal and external access rules.
If you are preparing a training session with your employees, our article on security awareness training programs will help get the most out of the upcoming session.
The Future of Secure Cloud Storage
Cloud storage is already considerably safer than an average on-prem server, and projections suggest that this difference in security will only get bigger. Here are several notable trends you can expect from cloud storage security in the near future:
- AI tools: Providers are gradually turning towards AI to help protect cloud data. An AI-powered tool can take the burden off staff members and oversee the first few levels of security analysis.
- The increase in multi-cloud storage: Storing second copies of data in alternate clouds will continue to increase in popularity as providers seek ways to mitigate the threat of ransomware and improve cloud disaster recovery.
- Better performance: Besides the security boosts, cloud storage solutions will also become more scalable and flexible to rival on-prem setups.
- Lower prices: Cloud providers will increasingly focus on reducing costs to make cloud storage more competitive. The likely first change will be the removal of hefty egress fees.
- The move towards the edge: We will see more cloud consumers move their cloud storage toward the network's edge. Edge computing enables clients to set up and run processes closer to the customer base.
- Confidential computing: More providers will start using confidential computing to make cloud storage security even more robust. This capability expands at-rest and in-transit encryption with additional in-use encryption that keeps data safe during operations.
Get on board with the latest standard for cloud security with PNAP's confidential computing infrastructure and ensure end-to-end protection of your valuable data.
The Right Service Provider is Vital to Cloud Storage Security
You should now be able to tell apart secure cloud storage platforms from those that lack adequate protection. Choosing a vendor that offers most (or, ideally, all) of the aforementioned capabilities will enable you to reap the benefits of cloud computing without adding unnecessary risk to your day-to-day operations.