Creating a Cloud Security Policy
Any company that wishes to protect its cloud assets needs a cloud security policy. A policy helps keep cloud data safe and grants the ability to respond to threats and challenges quickly.
This article explains the value of cloud security policies. Read on to learn what these policies cover, what benefits they offer, and how to write one for your business.
What Is a Cloud Security Policy?
A cloud security policy is a formal guideline under which a company operates in the cloud. These instructions define the security strategy and guide all decisions concerning the safety of cloud assets. Cloud security policies specify:
- Data types that can and cannot move to the cloud
- How teams address the risks for each data type
- Who makes decisions about shifting workloads to the cloud
- Who is authorized to access or migrate the data
- Regulation terms and current compliance status
- Proper responses to threats, hacking attempts, and data breaches
- Rules surrounding risk prioritization
A cloud security policy is a vital component of a company’s security program. Policies ensure the integrity and privacy of information and help teams make the right decisions quickly.

The Need for a Cloud Security Policy
While cloud computing offers many benefits, these services come with some safety concerns:
- Lack of security controls in third-party setups
- Poor visibility in multi-cloud environments
- Ample room for data theft and misuse
- Clouds are common targets for DDoS attacks
- Attacks quickly spread from one environment to another
Risks of cloud computing touch every department and device on the network. Therefore, protection must be robust, diverse, and inclusive. A reliable cloud security policy provides all those qualities. If a company relies on cloud services, outlined practices grant a level of visibility and control needed to protect cloud data.
Cloud Security Policies vs. Standards
Cloud security standards define the processes that support the execution of the security policy. Security policies and standards work in tandem and complement each other.
Standards cover the following aspects of a company’s cloud computing:
- Use of cloud platforms for hosting workloads
- DevOps models and the inclusion of cloud applications, APIs, and services in development
- Segmentation strategies
- Asset tagging and classifying
- Processes for evaluating asset configuration and security levels
Typically, policy rules are static. Standards are dynamic, and you should revise them often to keep up with the latest technologies and cyber threats.
Please refer to our article Security vs Compliance for a more in-depth analysis of the core differences between these two important terms.
Consider implementing phoenixNAP Confidential Computing Solutions to stay on top of new standards for cloud security.
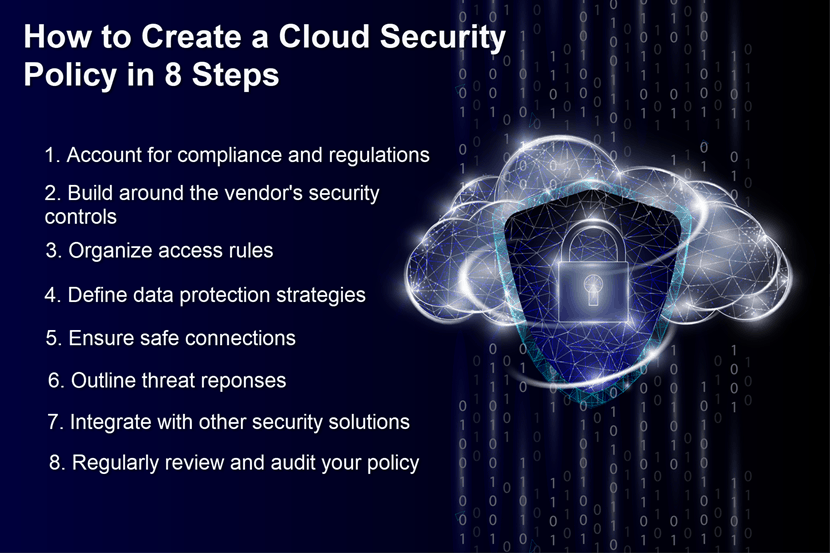
How to Create A Cloud Security Policy (8 Steps)
Before you start creating a policy, ensure you fully grasp your cloud operations. Knowing your systems before writing policies to address them saves you from unnecessary revisions.
Step 1: Account for Relevant Laws
If your company must adhere to some privacy or compliance regulation, consider how they affect the cloud security policy. All cloud-based activities must conform to legal obligations.
Step 2: Assess the Security Controls of the Cloud Vendor
Different providers offer different levels of security control. Inspect your partner’s security practices and form solutions that align with the offering.
Step 3: Assign Roles and Access Rights
Specify clear roles for your personnel and set their access to applications and data. Give employees access only to the assets they need to perform their tasks. Additionally, define how your company logs and reviews access.
Step 4: Protect Your Data
Determine how you will protect company data. Most businesses choose to encrypt all sensitive data moving through the cloud and the Internet. You should also document security rules for internal and external data stores.
Typically, providers offer Application Program Interfaces (APIs) as part of their services. Consider using an API to enforce encryption and Data Loss Prevention (DLP) policies.
Step 5: Defend the Endpoints
A single infected endpoint can lead to data breaches in multiple clouds. Therefore, you must set clear rules surrounding connections with the cloud to avoid this issue. This step includes secure sockets layers (SSLs), network traffic scanning, and monitoring rules.
Step 6: Define Responses
A policy must not only cover prevention. Consider ideal ways for teams to handle data breaches, outline reporting processes, and specify forensic functions. It also helps if you establish protocols for disaster recovery.
Step 7: Ensure Good Integrations
If you have multiple safety solutions, ensure the team integrates them properly. Poorly combined solutions create vulnerabilities, so find a way to integrate and leverage your company’s security devices.
Step 8: Perform Security Audits
Conduct regular reviews and upgrade components to remain ahead of the latest threats. Also, perform routine checks of the vendor’s SLAs so that you do not get blindsided by a problematic update on that end.
Cloud Security Policy Principles to Abide By
Keep it Simple
All employees must be able to understand the policy. Avoid overcomplicating and make the guideline clear and concise. Keeping it simple helps all workers follow the rules, and you also keep training costs down.
Start every policy with a definition of intent. The intent should clearly outline the point of the rule to help workers understand and navigate the regulations.
Make Rules Transparent
All teams responsible for enforcing and complying with the policy should have full access to the guidelines. Establish a record that those involved have read, understood, and agreed to abide by the rules.
Strategically Limit Access
Internal control regulations prevent unauthorized access to your cloud assets. Follow the Zero Trust model and only allow access to individuals who have a real need for resources. Some workers need read-only access, like those in charge of running reports. Other users must be able to do some ops tasks, such as restart VMs, but there is no reason to grant them the ability to modify VMs or their resources.
Monthly Data Encryption Updates
Schedule monthly data encryption updates. Regular updates ensure cloud resources safety, and thus you find peace of mind knowing everything is up to date.
Monitor Cloud Environments
Monitoring should be one of the major aspects of your policy. Cloud monitoring tools offer an easy way to spot activity patterns and potential vulnerabilities.
Make the Policy Employee-Friendly
Do not disrupt the company’s workflows with a cloud security policy . Try to create rules that align with your culture and help employees work more smoothly. If your policies interfere with day-to-day work too much, there is a chance some people will start to take shortcuts.
Gather Input Across the Company
A policy should not be the responsibility of a single team. The best guidelines come from multiple departments working together.
Gather advice from stakeholders across business units. This tactic provides a clear picture of current security levels and helps find the right steps to improve protection.
Do Not Outsource Your Policy
Delegating the policy building process to a third party is a mistake. While your cloud service provider can handle the task, the safest cloud security policies come from in-house efforts.
Go With Group Instead of Individual Access
Create administrative groups and assign rights to them rather than the individual. Group access makes daily tasks easier without compromising security.
Consider Two-Factor Authentication
Most major cloud providers allow the use of two-factor authentication (2FA). Use 2FA to protect new deployments and further defend from malicious login attempts.
Strict Restrictions
Some workloads only service customers or clients in a single geographic region. Consider adding an access restriction in those scenarios. Restricting access to a specific area or IP address limits exposure to hackers, worms, and other threats.
Use Keys Instead of Passwords
Consider making Public Key Infrastructure (PKI) a part of your cloud security policy. PKI protocols use a public and private key to verify user identity before exchanging data. Switching to PKI removes the danger of stolen passwords and prevents brute force attacks.
A Cloud Security Policy is a Must for Any Careful Company
The cost of fixing a data breach far outweighs the price of proper precautions. A cloud security policy provides appropriate cautionary steps when operating on the cloud. This policy allows you to leverage the cloud’s advantages without taking on unnecessary risks.