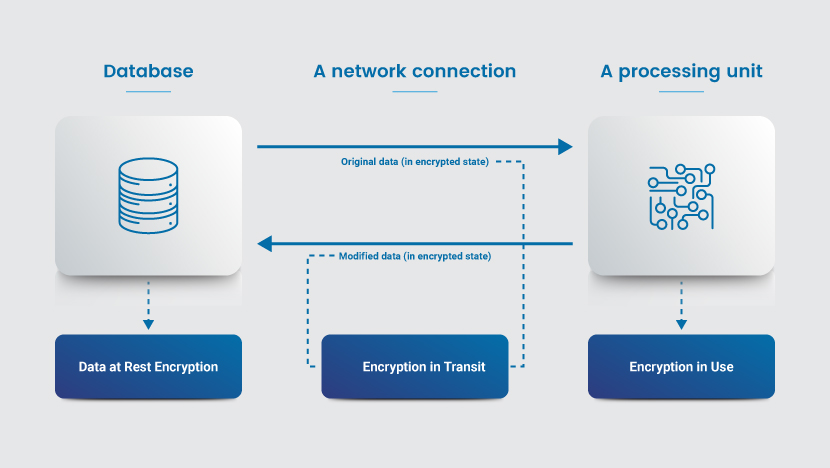
The two main encryption strategies (encryption at rest and in transit) do not keep data safe while files are in use (i.e., when accessed or consumed by a user or application). In-use data must be in plaintext to be read or understood, which makes whatever files are being processed a prime target for attacks.
This article is an intro to encryption in use, a practice that enables data processing while files are in ciphertext. Jump in to see how encryption in use works and how it addresses a major limitation of traditional encryption.

What Is Encryption in Use?
Encryption in use is the cybersecurity practice of encrypting in-use data (i.e., files that are being actively input, updated, accessed, read, or processed). Other common names for encryption in use are in-memory encryption and runtime encryption.
In typical computing scenarios, data must be decrypted before processing. Conversion to plaintext temporarily exposes data in its unencrypted form, which poses a major security risk. Encrypting in-use data addresses this vulnerability by allowing computations to run directly on encrypted files without the need for decryption.
There are two primary types of encryption in use:
- Partially homomorphic encryption (PHE). This type of encryption allows a computer to perform only one type of mathematical operation (either addition or multiplication) on encrypted data. The process cannot support both operations together.
- Fully homomorphic encryption (FHE). This type of encryption allows arbitrary sequences of both addition and multiplication operations on encrypted data. Fully homomorphic encryption is more versatile than PHE but has higher computational requirements.
A subset of FHE is the so-called secure multi-party computation. This encryption type enables collaborative data processing among multiple parties, each holding a share of the encrypted data.
Encrypting in-use data is valuable in various use cases, but the practice is essential in scenarios where sensitive data is:
- Processed by a third-party service provider.
- Frequently transferred between different processing components of a system.
- Processed in a multi-tenant cloud computing environment.
Encrypting in-use data is computationally intensive. The process requires the computer to encrypt and decrypt data in real-time, which often introduces performance overhead. This issue is a major reason why most adopters process data in the public cloud, a strategy that grants access to sufficiently powerful hardware.
Market Research Future (MRFR) predicts that the data encryption market will reach a value of $38.7 billion by 2030 (a 16.3% CAGR). The growing adoption of encryption in use will be a significant driver in reaching that figure.
How Encryption in Use Works?
Encryption in use enables computations on ciphertext in a way that, once you decrypt data, the output is the same as if the computer operated with plaintext files.
Here's an overview of how this process works:
- The CPU loads data into memory for processing.
- The app that processes data defines a private region of main memory (a so-called trusted execution environment (TEE) or enclave).
- Data in an enclave cannot be read or written by any process from outside the enclave (regardless of privilege level or CPU mode).
- The computer encrypts the enclave memory using keys stored within the CPU. The two most common encryption algorithms for THE are the Fast Fully Homomorphic Encryption over the Torus (TFHE) and Simple Encrypted Arithmetic Library (Microsoft SEAL).
- The encryption happens dynamically and in real-time as the memory reads and writes data.
- Data decryption only occurs within the CPU for code within the enclave, preventing access even to the operating system.
- The CPU processes the enclave-based data while maintaining its encrypted state.
Encrypting in-use data scrambles files without impacting the device's ability to process data (although it does prolong the process). There are two main ways companies can adopt this practice:
- Hardware-based encryption. Some computers have specialized components that provide built-in TEEs. For example, Intel SGX (Software Guard Extensions) and AMD SEV (Secure Encrypted Virtualization) have this feature.
- Software-based encryption. Encryption libraries and algorithms within the computer's software handle the encryption and decryption processes during data processing.
Users and apps interacting with the computer are not aware of encryption in use. From their perspective, data is handled in its standard, readable form. Yet, if an attacker accesses the computer's memory during active processing, they won't reach any plaintext data.
As with encryption at rest and in transit, encryption in use is only as effective as your key management procedures.
Benefits of Encryption in Use
Encrypting in-use data provides several benefits for organizations trying to enhance security posture. Here are the main selling points of this type of encryption:
- Encryption during data's entire lifecycle. Encryption in use mitigates the main vulnerability of at-rest and in-transit encryption. Between the three precautions, there's no window of opportunity for intruders to steal plaintext data.
- Mitigation of memory scraping attacks. Memory scraping attacks involve extracting sensitive info directly from a computer's memory. Encrypting in-use data means that, even if someone gains access to the memory (which is relatively easy for a tech-savvy hacker to do), the attacker will only steal encrypted data.
- Secure processing in untrusted environments. Encryption in use provides an extra layer of security when data processing occurs in untrusted or potentially compromised environments. A common example is a large enterprise network full of potentially compromised devices (e.g., malware-infected BYOD or shadow IT devices).
- Safe outsourcing. Encrypting in-use data enables organizations to leverage third-party services for data processing without exposing raw, unencrypted data. Organizations get to use data processing and analytics services without risking sensitive data.
- Secure cloud computing. While highly useful, public cloud services are multi-tenant environments that process data at remote servers. Encryption in use protects processed data from potential vulnerabilities or breaches in the cloud infrastructure.
- A boost to data integrity. While the primary focus of encrypting in-use data is confidentiality, this practice also contributes to data integrity. Any unauthorized modification during processing results in an invalid output once data is decrypted.
- Compliance with data protection regulations. Many data-related regulations require encryption to ensure the security and privacy of sensitive info. While not mandatory for compliance, encrypting in-use data helps meet the expectations of both GDPR and HIPAA.
Encryption in use significantly lowers the chance of an organization suffering costly data breaches or leaks.
Challenges of Encrypting In-Use Data
While encrypting in-use data improves security, the practice presents several challenges potential adopters must know about.
Here are the main issues and drawbacks of encryption in use:
- Computational overhead. Real-time encryption and decryption during data processing introduces computational overhead. This overhead leads to a slight-to-mid decrease in system performance, particularly in processing-intensive apps or resource-constrained environments.
- Limited operations. Not all types of computations can be efficiently performed on encrypted data. Certain operations (such as those involving complex branching logic) are challenging, impractical, or impossible to implement.
- Data size increase. Encryption in use significantly increases the size of processed data. This issue often leads to additional storage or bandwidth requirements.
- Limited protection against authorized entities. Encrypting in-use data doesn't prevent authorized users or processes from accessing and manipulating plaintext data. Adopters must add additional security measures to address potential insider threats.
- Compatibility challenges. Ensuring compatibility between different systems and components is often challenging. Interoperability issues may arise if encryption protocols or algorithms differ, plus existing systems and apps often require substantial modifications.
- Key management complexity. Managing encryption keys during their lifecycle (generation, distribution, rotation, revocation, retirement, etc.) is complex and time-consuming when you use encryption at rest, in transit, and in use.
Our Encryption Management Platform is an all-in-one EMP that centralizes encryption management and enables you to control all keys from a single pane of glass.
Who Needs Encryption in Use?
Encryption in use is beneficial for a wide range of organizations that prioritize the security of sensitive data. Here are the usual adopters:
- Companies that utilize public cloud services for data processing.
- Businesses that operate e-commerce platforms and process customer payment info, personal details, and transaction data.
- Service providers and software companies that want to bolster the security of their offerings (either for internal data protection or as a further selling point for customers).
- Enterprises that must adhere to international data regulations and standards.
- Companies that extensively collaborate with suppliers, business partners, or other stakeholders on data processing.
- Organizations that store and process sensitive customer data (e.g., hospitals, banks, or credit unions) or client info (e.g., legal firms or consulting agencies).
- Companies that safeguard intellectual property, such as proprietary info or research data.
- Businesses with remote or mobile workforces that process data outside the corporate network (or on personal devices within the corporate network).
Most adopters of encryption in use operate in high-risk industries, such as finance, government, or healthcare.
Healthcare is a go-to target for cyber-attacks due to the high value of patient data and the critical nature of health-related services. Learn more about the risks of this industry in the following articles:

Encryption in Use and Confidential Computing
Confidential computing is a security paradigm that aims to protect data during its entire lifecycle and guard sensitive info from unauthorized access or disclosure. While not synonymous with encrypting in-use data, confidential computing incorporates all three layers of encryption as a fundamental precaution.
Confidential computing relies on the use of secure enclaves within a CPU. Enclaves facilitate the encryption and protection of data during active processing, plus ensure no one or nothing has access to the processed data (not even the OS or hypervisor).
There are two main approaches to confidential computing:
- Application software development kits (SDKs). In this approach, developers are responsible for dividing an app into untrusted and trusted code. The untrusted code runs normally, while the trusted code runs within an enclave.
- Runtime deployment systems. This approach to confidential computing enables apps to run in an enclave without requiring code rewrites for a particular hardware or platform.
The SDK approach allows for better scrutiny of the trusted code but requires teams to change the app. Meanwhile, cost reductions and time to value (TTV) are the two selling points of the runtime deployment system-based approach. However, deploying unmodified apps often limits the choice of features.
Our confidential computing offering enables you to easily apply end-to-end data encryption (at rest, in transit, and in use) to all sensitive files. Confidential computing is available on pNAP's dedicated servers and Bare Metal Cloud (BMC), as well as to users of our Data Security Cloud (DSC).
A Soon-To-Be Data Protection Standard
While still not as widely used as the at-rest and in-transit counterparts, encrypting in-use data is already a vital enabler. The practice allows companies to run data computations in the cloud, perform collaborative analytics, make the most of remote teams, and enjoy safer service outsourcing. Expect encryption in use to soon grow into a data security norm as the tech becomes more efficient and practical to adopt.



