CommonSpirit Health Ransomware Attack Explained
CommonSpirit Health, the second largest non-profit hospital chain in the U.S., was the target of a devastating ransomware attack in October 2022. The sheer scale of the incident forced the organization to share details about the breach, something healthcare providers typically avoid doing, offering valuable lessons on how not to prepare for and respond to a ransomware attack.
This article breaks down the recent CommonSpirit Health ransomware attack, one of the most notable cybercrime incidents of 2022. Jump in to learn exactly how the attack unfolded and see what CommonSpirit Health could have done better before and during the incident.

Learn about the different types of ransomware and see what strategies criminals use to encrypt files and pressure victims into paying for the decryption key.
What Happened During the CommonSpirit Health Ransomware Attack?
On October 2, 2022, CommonSpirit's security team detected strange activity on several networks. According to the organization's recap of events, the team immediately took steps to:
- Boost network security.
- Take systems offline to isolate the threat.
- Bring in third-party cybersecurity specialists to investigate the incident.
Malicious activity and precautionary system shutdowns interrupted access to electronic health records (EHRs), forcing facilities in multiple regions to delay patient care. Hospitals and care sites in several states reported interruptions, including:
- Nebraska.
- Tennessee.
- Texas.
- Washington.
- Iowa.
CommonSpirit acknowledged the attack publicly three days later, on October 5. The organization did not comment on the nature of the breach, describing the problem as an "IT security issue" and not ransomware. At that time, CommonSpirit refused to say whether intruders reached any patient info or health data.
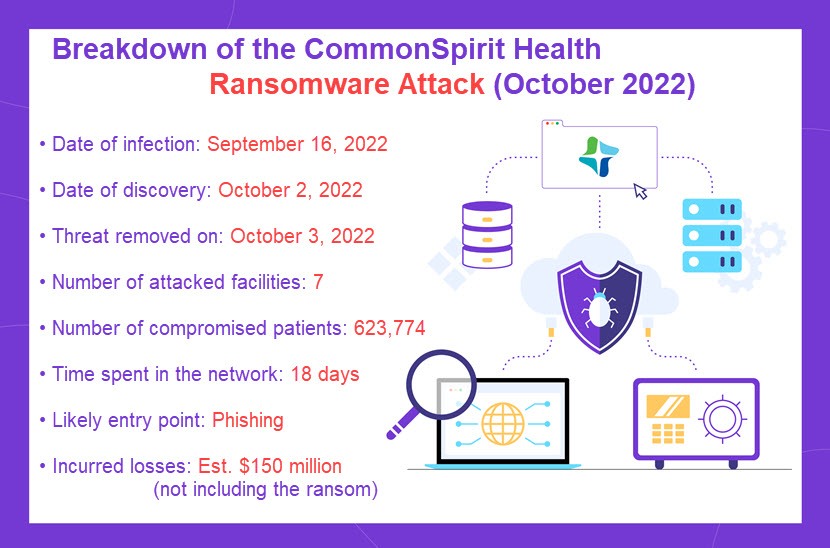
Two months later, in a December 2022 update, CommonSpirit confirmed that the organization faced a ransomware attack. Threat actors infiltrated portions of the network between September 16 and October 3. During that time, criminals gained access to the personal data of patients who received care at Franciscan Health, a 12-hospital affiliate of CommonSpirit Health.
As of March 2023, the healthcare provider has not yet attributed the attack to a particular ransomware group. No criminal organization is taking credit either, so the identity of the threat actor remains a mystery to the public.
While CommonSpirit still refuses to acknowledge how malicious software entered its networks, experts suspect criminals used phishing to compromise an account of a high-level administrator. Speculative "post-mortems" suggest the two most likely targets are:
- The hospital domain admin.
- The database record admin.
Once inside the network, intruders had around 18 days to compromise other accounts and move laterally through systems in search of protected health information (PHI).
A ransomware attack that encrypts PHI is a HIPAA breach you must report to the Office for Civil Rights (OCR). However, if a breach risk assessment proves a low probability of compromise, the OCR will not rule the incident a HIPAA violation.
Who Was Affected by the CommonSpirit Health Data Breach?
CommonSpirit revealed that threat actors reached the personal data of individuals who received care at the seven Franciscan Health hospitals in Washington state (plus several associated physician clinics). Here's a list of the affected facilities:
- St. Anne Hospital, formerly Highline Hospital (Burien).
- St. Michael Medical Center, formerly Harrison Hospital (Bremerton & Silverdale).
- St. Joseph Hospital (Tacoma).
- St. Francis Hospital (Federal Way).
- St. Anthony Hospital (Gig Harbor).
- St. Elizabeth Hospital (Enumclaw).
- St. Clare Hospital (Lakewood).
Intruders accessed the personal data of 623,774 patients during the CommonSpirit Health ransomware attack. Hackers also gained unauthorized access to personal data belonging to family members and caregivers of patients.
All seven Washington-based facilities had to shut down EHRs, forcing hospitals to reschedule surgeries and appointments. Other hospitals also felt the indirect effects of the incident. The following facilities reported issues:
- Seattle-based Virginia Mason Franciscan Health providers.
- MercyOne Des Moines Medical Center.
- CHI Health facilities in Nebraska and Tennessee.
- Houston-based St. Luke's Health.
- Michigan -based Trinity Health System.
Restoring systems to a pre-incident state was slow and challenging. Most hospitals recovered within two to three weeks, but a few still did not have all EHR systems back online on November 9 (more than a month after the attack).
CommonSpirit also suffered staggering financial losses at this time. While the organization refuses to answer whether it paid the ransom, the provider incurred an estimated $150 million in losses due to the attack. This figure includes:
- The cost of restoring IT systems to pre-incident state.
- Lost revenue from the business interruption.
CommonSpirit is also facing a class-action suit alleging negligence played a role in the ransomware attack. A Washington state patient filed the lawsuit on December 29, 2022, blaming the provider for failing to "exercise reasonable care" and placing patients at an increased risk of identity theft.
What Data Was Compromised?
The CommonSpirit Health ransomware attack enabled hackers to access the sensitive data of over 620,000 patients, as well as their family members and caregivers. Criminals managed to reach:
- Names.
- Addresses.
- Phone numbers.
- Dates of birth.
- Unique IDs used internally by the organization (not the Medical Record Number or insurance ID).
While CommonSpirit continues to claim that there's no evidence hackers "misused" any personal info, this data is a gold mine for identity theft. In most cases, criminals sell that type of data to the highest bidder or simply post it on the dark web.
If hackers managed to exfiltrate data before encryption, chances are we'll be seeing the effects of this attack for years to come.
Stealing sensitive data is a common goal of hackers, but not the only one. Learn about the different types of cyberattacks and see what each of them aims to accomplish.
How Could the CommonSpirit Health Ransomware Attack Be Prevented?
CommonSpirit Health operates 142 hospitals and over 2,200 care sites within 21 states. This immense attack surface is challenging to protect, but the organization should have invested more time and effort into ransomware prevention.
Here's what the provider could have done better before and during the CommonSpirit Health ransomware attack:
- Lackluster network security: Since hackers spent 18 days moving between systems, chances are the provider did not invest in network segmentation, strict access controls, intrusion detection systems (IDSes), or zero-trust security measures.
- Inefficient response: The lack of an effective incident response and disaster recovery plan prevented the organization from quickly restoring operations. Reports suggest the provider took more than two weeks after the start of the attack to restore limited EHR functions. Two weeks are way off the acceptable RTO for such critical systems.
- Poor phishing defenses: Since criminals used phishing to create an entry point into the network, chances are the provider did not invest heavily in email security or employee security awareness training. Phishing attempts are relatively easy to stop with email filtering and teaching the staff to recognize signs of suspicious messages (unfamiliar greetings, grammar errors, non-matching addresses and domain names, unusual requests, etc.).
- No at-rest encryption: If the provider used encryption at rest to protect stored data, the attackers would not be able to steal PHI even after data exfiltration. Chances are the organization also lacked up-to-date data backups judging by how long the provider took to restart operations.
- No third-party expert support: According to reports, CommonSpirit Health reached out to security experts only after they identified suspicious network activity. If your in-house team lacks the necessary know-how to prevent ransomware, hiring third-party specialists is a no-brainer investment (and a significantly smaller one than what criminals ask for decryption keys).
Concerned about ransomware attacks? You're not paranoid—ransomware accounted for over 20% of all cybercrime in 2022. Protect yourself from this cyber threat with pNAP's ransomware protection and our unique mix of immutable data backups and cloud-based disaster recovery.

Ransomware Attacks in Healthcare
Healthcare providers are no strangers to ransomware attacks. Despite some security improvements in recent years, hospitals remain one of the most common targets for this type of cybercrime.
Here are a few stats that demonstrate the danger ransomware attacks pose to the healthcare industry:
- Around 66% of all hospitals in the US were the target of a ransomware attack at some point in 2022.
- Two in three healthcare IT professionals report a "significant cybersecurity incident" in the past 12 months.
- The average recovery time for a healthcare provider following a ransomware attack is one week. This number was slightly lower in 2021 (around 6.2 days).
- The average cost of fully restoring services and systems to a pre-ransomware state was $1.85 million in 2022.
- In 2022, healthcare providers paid the ransom in about 61% of ransomware incidents. No other industry had a higher rate.
- Healthcare providers paid an average ransom of around $197,000 in 2022, the lowest of any sector. However, the average ransom demand in healthcare was "only" $16,000 in 2020.
- The average healthcare data breach now costs $10.1 million, the highest of any industry.
- Hospital security teams take an average of 232 days to detect a breach and an additional 85 days to contain the threat.
- There were 24 successful ransomware attacks on US-based healthcare providers in 2022 (incidents affected a total of 289 hospitals). Criminals stole files and threatened to cause a data leakage in 17 out of 24 confirmed attacks.
- Almost 22% of healthcare organizations believe that ransomware had a direct impact on patient mortality rates in 2022.
- Three in four ransomware attacks on hospitals lead to operational disruptions, such as canceled surgeries and extended hospital stays.
- Experts predict the global cost of ransomware attacks on the healthcare industry will exceed $25 billion by 2025.
Continue learning about ransomware attacks in healthcare and see why hospitals will remain a go-to target for the foreseeable future.
Learn from the CommonSpirit Health Ransomware Attack
While we still do not have all the details surrounding the incident (and we likely never will), it's clear the recent attack was devastating to CommonSpirit Health. Reports of high losses, reputation hits, and looming lawsuits are pressuring the hospital chain despite the decision to remain tight-lipped about recent events. Prepare for ransomware attacks instead of risking a similar scenario for your business.