What is UPnP (Universal Plug and Play)?
While UPnP eliminates the need for extensive setups when adding a new device to a local network, this protocol can introduce considerable risk to your data and operations. The ability to connect devices quickly is convenient, but the speed of UPnP often comes at the price of cybersecurity.
This article is an intro to UPnP (Universal Plug and Play) and the security risks associated with this network protocol. Read on to learn how this protocol works and see how hackers exploit UPnP to bypass firewalls and create an entry point into the target network.

What is UPnP?
UPnP (Universal Plug and Play) is a networking protocol that enables devices to discover each other and connect without the need for manual configuration or user intervention. The protocol automates all the steps necessary for recognition and communication between devices on the same network.
The main goal of UPnP is to provide an automated way for adding and connecting new hardware to a local network. The protocol enables a device to join the network by:
- Setting up the device's IP address.
- Broadcasting the device's name and capabilities to the rest of the network.
- Informing the new piece of hardware about the capabilities of other connected devices.
- Enabling network devices to communicate and function in tandem.
What Is UPnP Used For?
Some of the most common use cases for UPnP include:
- Connecting a new printer to every PC and tablet in the household.
- Connecting a gaming console to a game server to play and stream online games.
- Streaming content from a computer to a smart TV.
- Linking a wireless speaker set to a mobile phone.
- Connecting to the home surveillance system to keep an eye on the house while you are away.
- Connecting and remotely controlling an IoT system from a mobile device (smart lighting, internet-controlled thermostats, smart locks, etc.).
While convenient, the UPnP protocol is not free of risks. If the protocol permits a device with a critical vulnerability or malware to join, a skilled hacker can create a permanent entry point into the local network. This security risk is why UPnP is typically enabled only on residential setups and not small business or enterprise networks.
Both residential and business networks require protection. Read about the basics of network security and see how experts keep malicious actors away from valuable devices and data.
How Does UPnP Work?
UPnP enables apps and devices to automatically open and close ports to connect with the LAN network. This process (known as port forwarding or port mapping) happens on the router and can permit web traffic to pass through an internal network from an external source.
UPnP enables automatic, device-to-device port forwarding via four standards:
- Internet Protocol Suite (TCP/IP).
- Hypertext Transfer Protocol (HTTP).
- Extensible Markup Language (XML).
- Simple Object Access Protocol (SOAP).
Since the protocol relies on common networking standards, UPnP does not require any additional drivers or technologies to work. Most devices on the market can participate in UPnP regardless of their OS, programming language, or manufacturer.
From the user's perspective, UPnP is a simple process. You bring home a new device, connect it to the network, and your other devices can instantly communicate with the latest piece of hardware. However, the process is far more complex in the background, and UPnP goes through six phases whenever you set up a new device:
- Addressing.
- Discovery.
- Description.
- Control.
- Eventing.
- Presentation.
The protocol relies on a client-server model where UPnP control points (clients) search for UPnP servers (devices) that provide services. Below is a closer look at what happens at every phase of the UPnP protocol.
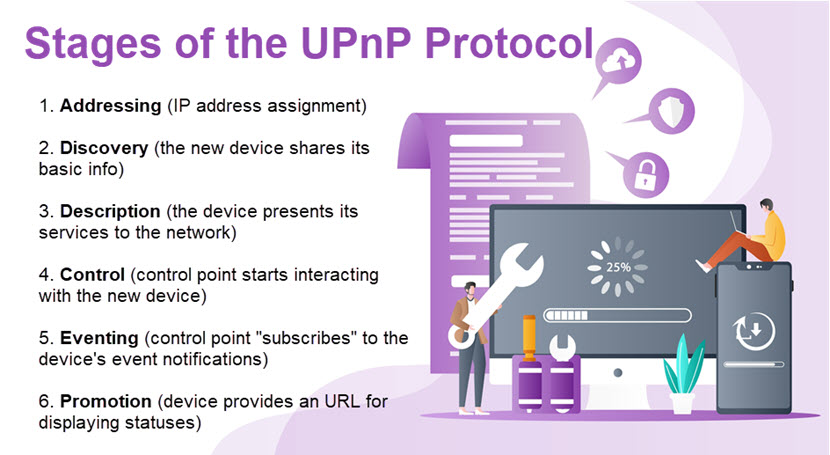
Addressing
The new device must have a unique IP address to become a part of the network, so the UPnP either:
- Requests an IP address for the new device from the Dynamic Host Configuration Protocol (DHCP) server.
- Enables the device to use a process called AutoIP to self-assign an IP (if there is no DHCP server).
If the device gets a domain name during the DHCP transaction (for example, through a DNS server or via DNS forwarding), the device will use that name in network operations.
Not all IoT devices require an IP address, such as internet-connected coffee pots, thermostats, and light bulbs. Instead, these devices communicate with the network through technologies like Bluetooth or Radio Frequency Identification (RFID).
Discovery
The device uses Simple Service Discovery Protocol (SSDP) to present its details to network control points. The new device sends SSDP alive messages with basic specifics about its:
- Device type.
- Identifier.
- Pointer (network location).
Depending on the UPnP setup, the network control point can actively search for devices of interest or listen passively to SSDP messages.
Description
Once a control point discovers a device, the network must learn about its capabilities before interacting with the new piece of hardware. The device sends a detailed description that includes:
- Info about the vendor.
- Model name.
- Serial number.
- A list of any services.
- Presentation URLs for vendor-specific websites (optional).
The device sends these messages in XML format, and the network creates a Device Description document that lists the URLs for control, eventing, and service description. Each service description also includes the commands to which the service can respond and parameters for each action.
Control
Before the control point can start interacting with the discovered device, the network sends messages for invoking actions on services. These control messages are also in XML format and use the Simple Object Access Protocol (SOAP).
Event Notification (Eventing)
UPnP has a protocol called General Event Notification Architecture (GENA) that enables a control point to register itself as a service to get notifications for device state changes.
The service sends an event notification to all registered control points whenever a state variable changes. These simple event messages are in XML format and contain only the status variables and their current value.
Presentation
If the new device provides a presentation URL in the description phase, the control point can retrieve a page from this URL and load it into a web browser. In some cases, the user may control the device or view its status through the browser.
The degree to which a user can interact with a device through the presentation URL depends on the specific capabilities of the web page and device.

Is UPnP Safe and What Security Risks Does It Have?
Despite the benefits of UPnP, the protocol has two major security risks:
- By default, UPnP does not authenticate devices and merely assumes that every device is trustworthy.
- UPnP allows an entity outside the home network to poke holes in the router and access local devices without the traffic going through a firewall.
Since UPnP enables traffic to bypass security barriers, the protocol can lead to various security concerns if a malware-infected device manages to connect to the network.
Another security concern is that UPnP has no official implementation. Different routers have different applications, and many deployments come with unique UPnP-related bugs a hacker can exploit.
Unfortunately, many router manufacturers enable UPnP by default, making LAN-based devices discoverable from the WAN. Several high-profile UPnP-based attacks happened due to router-related flaws in port forwarding, such as:
- A Flash UPnP attack starts when a victim accesses a website running a specific Flash applet that sends requests to a faulty router to forward ports.
- Hackers behind the Mirai attacks went after routers with open telnet ports exposed due to enabled UPnP. Once they found a vulnerable router, hackers used credential stuffing to access the network and installed the Mirai malware on all local devices.
- The CallStranger vulnerability is also a result of a router-based UPnP flaw that can expose users to data loss.
The biggest weakness of UPnP is the automatic trust the protocol places on users and devices. Read about zero-trust security, a modern approach to cyber safety that relies on the exact opposite strategy to keep a network safe.
How Do Hackers Exploit UPnP?
Hackers take advantage of overly trusting UPnP protocols in different ways. Most exploits require the hacker to first breach a network in some way (for example, via brute force or a phishing email) to install malware on the system. Following malware injection, an attack can look like this:
- The malicious program pretends to be a LAN device (such as an Xbox or a smart TV).
- The program sends a UPnP request to your router.
- The router opens the port and allows a virus or worm to install on the target network (even though the firewall would stop such traffic in normal circumstances).
- Hackers get a backdoor into your network and can install whatever program or run any script they choose.
Backdoors from UPnP flaws can remain undetected for months, so criminals have ample time to fulfill their goals. The most common objectives are to:
- Spread malware to other devices.
- Steal sensitive data and cause a data breach.
- Encrypt data at rest and start a ransomware attack.
- Get remote access to other network devices (most commonly to control or hijack an IoT device).
- Use the router as a cover or proxy for other cybercriminal activities (typically to turn devices into bots for a Distributed Denial of Service (DDoS) attack).
- Modify administrative credentials.
- Change PPP, IP, or Wi-Fi settings.
- Spy on network activity and relay info back to the hacker.
- Change DNS server settings (typically to load a decoy credential-stealing website instead of a legitimate website).
- Imitate devices with high privileges to move laterally and reach other network segments.
These risks are not exclusive to UPnP. PhoenixNAP's offerings for ransomware prevention, end-to-end encryption, and DDoS protection can keep you a step ahead of cybercriminals.
Should You Disable UPnP?
If security is your priority, there is no real reason to leave the UPnP on. It is too difficult to differentiate between malicious and legitimate UPnP requests, which is why security-aware users typically keep the protocol off as a cybersecurity best practice.
If port forwarding is an essential requirement for your use case (for example, if you have a VoIP program, peer-to-peer app, game server, etc.), a far safer option than UPnP is to manually forward each port. Manual port forwarding ensures you control each connection and do not risk malicious actors or programs exploiting the behind-the-scenes automation of UPnP.
The only scenario where relying on UPnP is a sensible choice is running a simple home network without sensitive data or systems. There will still be risks, though, and you will need to keep the entire attack surface associated with UPnP up to date, including:
- Routers.
- Firewalls.
- Antivirus and malware software.
- All connected IoT devices.
If you turn the UPnP off, remember that your network will no longer automatically open ports on your LAN. The router will ignore even legitimate requests, so you will need to set up the port forwarding rules for each connection manually.
Another safer option is to use the non-standard solution called UPnP-UP (Universal Plug and Play - User Profile). This version has an extension for user authentication the original protocol lacks. Unfortunately, while UPnP-UP is far safer than the standard version of the protocol, not all devices support UPnP-UP.
Do Not Prioritize Convenience Over Security
While UPnP fulfills a genuine need, the protocol has serious design flaws that can compromise every device on the network. Unless UPnP is essential to your operations, you should turn the protocol off. The router will ignore all incoming requests and you will need to set up new devices manually, but your security is worth the extra effort.