The Definitive Guide to Bare Metal Servers
A single tenant physical server, or bare metal server, can form the base of a secure, powerful, and stable digital infrastructure. Many of the potential shortcomings associated with a shared virtual environment are non-factors in the bare metal environment.
Bare metal virtualization offers an uncompromising experience. Resources are more readily available, network latency is minimized for better performance, and the tenant enjoys root access. Bare metal is highly customizable, and the tenant may optimize the server based upon their individual needs.
The guide below serves as a detailed introduction to the bare metal environment. After reading this article, you should be able to make an informed decision about the utility of bare metal servers and how it fits within your IT infrastructure.
What is Bare Metal Server?
A bare metal server is a physical computer specifically designed to run dedicated services without any interruptions for extended periods. It is highly stable, durable, and reliable.
Bare metal servers are a single-tenant environment, meaning that a single server’s physical resources may not be shared between two or more tenants.
Because of this physical separation, bare metal servers are free of the “noisy neighbor” effect that haunts virtual environments. One significant benefit of this isolation is performance predictability. Thanks to this, bare metal servers feature the most stable environment, making it perfect for processing large volumes of data.
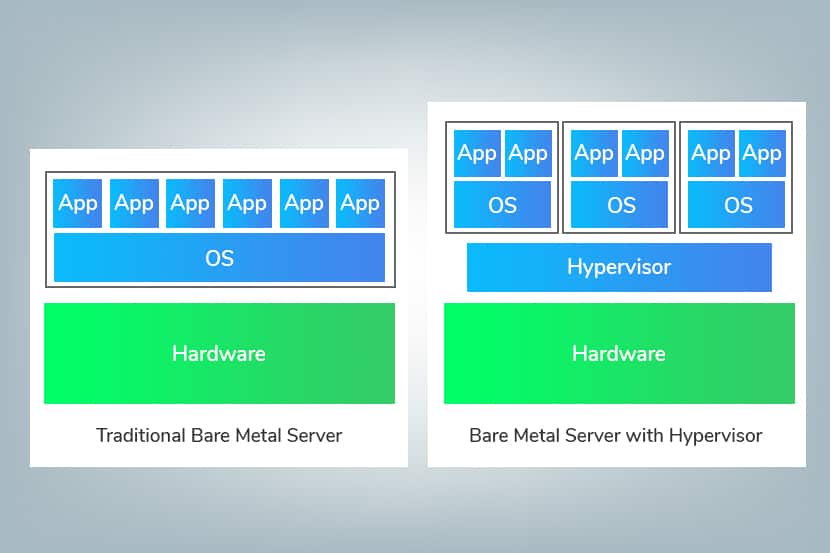
Other significant benefits include direct access to the server and the ability to leverage all underlying hardware architectures. Let’s explain the latter. If you provision a virtual machine (VM), you get a guest OS sitting on top of a hypervisor sitting on top of physical hardware. As a user, you would only have access to the guest OS and the management interface used to create the VM. You would not have direct access to physical hardware.
On the other hand, you have full access to the underlying architecture with a bare metal server. The benefit here is that you have more options available when creating your own platform to host a service or application. This leads us to another critical point.
Bare metal servers do not require the use of several layers of software, unlike the virtual environment, which has at least one additional layer of software – a Type 1 hypervisor.
This means there is one less layer of software between you and your physical hardware in everyday use. Hence you can expect better performance. It must be noted that bare metal tenants can create virtual machines on top of bare metal in a fashion similar to a virtualized environment.
Bare metal is like having your own house; you can customize it any way you want. You don’t have to deal with noisy neighbors.
In contrast, a public cloud multi-tenant virtualized environment is like renting an apartment. The neighbors’ kids drive you crazy with their yelling, and there’s not much you can do about that strange smell in the hallway.
Defining Bare Metal Environments
All environments, virtualized or bare metal, are based on physical hardware. So, even virtualized environments (e.g., public cloud) possess physical hardware underneath.
The term ‘bare metal’ is used mainly to differentiate a physically dedicated server from a virtualized environment and modern cloud hosting forms. Within a data center, bare metal servers are the ones not being shared between multiple clients.
It is important to remember that even a virtualized environment has physical hardware underneath. However, the shared hosting deployment model that is characteristic for virtual environments differentiates so that the end-user works with virtual resources, thus lacking access to the bare metal level.
The single-tenant of a bare metal server has root-level access. It is available for additional software options, which are not possible with a bare metal hypervisor.
Why Choose a Bare Metal Server?
Bare metal dedicated servers are great for small to medium businesses looking for a cost-effective hosting solution that can quickly automate and scale their resource allocation.
Many experts say that the use of bare metal servers is in decline compared to other hosting options. However, this type of server remains an extremely popular option, especially in many industries. The unique characteristics of the platform allow for an elite level of performance, power, and security.
In 2016, the market for bare metal servers was at a total value of approximately USD 1.3 billion. By 2025, it is expected to reach USD 26.21 billion. Source: Grandview Research
Industries that traditionally rely on dedicated hosting solutions and colocation are the banking and financial services industry, health care, and government. Additionally, bare metal is perfect for critical high-intensity workloads, such as business intelligence or database apps. Render farms and media encoding operations are examples of projects that use this option rather than virtualized servers because of the heightened performance levels.
Innovative software development companies use bare metal dedicated servers as an affordable way to test and launch products.
Industries with the highest needs for data security, world-class performance, and precise data operations are most likely to use bare metal systems. As the demand for storage grows alongside big data, this market will continue to grow with it. Large enterprises within these sectors are expected to drive the majority of usage. Up until 2016, the SMB market was a more significant consumer of the bare metal infrastructure.
The largest driver of growth over the entire market is expected to be advertising and emerging technological advancements.
Advantages
When using bare metal, you don’t have to compete with other users on the same system for resources.
All users can get high performance from this type of server. A dedicated server can deal with a more significant workload than a similar virtual machine in most cases. This makes dedicated hosting best for users who need top levels of performance.
Compared to other types of dedicated servers, bare metal is often easier to manage due to being in a data center. Most providers offer a range of setup options that can be customized to match your exact needs. Managing a server can be challenging and time-consuming. So, having a third-party manage your server for you can be a benefit for many companies.
Managed servers are also more cost-effective than on-site servers. Data centers are more streamlined than in-house setups. So, they can offer more at a lower cost. They also provide other benefits such as a higher bandwidth connection.
Most data centers also offer services that are very valuable to IT teams. Some examples of this are guaranteed uptime, 24/7 support, and regular security audits. Better yet, getting these services from a third-party means not having to hire in-house staff to perform them.
You can learn more about the differences between dedicated servers and public cloud in our post “Cloud vs. Dedicated Server: Which Is Best For Your Business?”
At the Forefront of New Technology
Companies are taking advantage of bare metal infrastructure to employ new technologies in exciting ways.
For instance, containers bring another level of performance capability to the bare metal environment. Running containers on top of bare metal servers provide an alternative to virtual machines (VMs).
Containers surpass VMs in resource usage, as every VM has its minimal overhead while containers use less memory. This makes containers on top of bare metal, the perfect environment for developing apps.
Large enterprises are beginning to experiment with concepts such as machine learning and AI. This type of computing emphasizes big data, mathematics, analytics, and visualization. Considering GPUs are the driving force of deep learning, bare metal’s data crunching and GPU capabilities make it the perfect platform for such tasks.
Understanding the basics of bare metal helps tremendously when trying to make sense of these new developments.
Flexible Hosting Options
Organizations can run bare-metal servers from in-house data centers, a colocation center, or partner with a managed service provider to lease a server.
Each of these options has its advantages and drawbacks, but leasing a bare metal server is the most cost-effective solution for small to medium organizations. Deploying leased servers is fairly quick nowadays, and most IT service providers offer pre-configured dedicated servers that are ready for any specialized workload.
For instance, secure bare metal servers based on Intel Xeon scalable processors are cost-effective enterprise-grade solutions ready for any intensive workload you can throw at them.
How Long Does it Take to Deploy a Bare Metal Server?
The average bare metal server takes longer to implement than a virtualized environment, which can be spun up in a couple of minutes. It can take anywhere between several hours and even up to a couple of days to provision a server as there is more customization that takes place.
Even though provisioning and maintaining a bare metal server may take more time, it all makes sense once its performance reliability proves to be a game-changer for your organization.
Server Access
Servers are accessed through a private network, and the tenant interacts with the device through remote desktop access. A private network connection is established via a VPN by connecting to a designated end-point. If you want to connect to a Linux-based server, you can do so through a Secure Shell (SSH) tunnel. This way, you can access a server as if it was physically on your workstation. For enhanced security, remote desktop access software encrypts on both the server’s end and your end.
Initially, you access the server as the root user. That’s the ‘all-mighty superuser’ who can do anything on the server. If you want to limit the danger of accidental changes, you will want to create a non-root user.
Managing a Bare Metal Server
There is a general belief that operating bare metal servers requires a large team of IT professionals. While this may be true for an on-premise solution, it may not necessarily be the case when it comes to colocation and leasing. Managed service providers offer a full range of additional services to help you run your online business. This means you can simplify your operations by outsourcing IT work to a service provider and focus on your business goals. For example, if you lease a fully managed dedicated server to resell hosting, you can concentrate on selling your services while your IT service provider handles everything else.
The extent to which you participate in managing the server may vary, but generally, you need to cover the following:
Updates and Patches
Regularly update the OS and perform software patches. This is what protects your bare metal server from malicious attacks. Also, run the chkrootkit, rkhunter, and clamav server application tools regularly.
Monitoring
You need to monitor key operational metrics of the server, switches, firewalls, etc. Set up early thresholds and alarms that will notify when a threshold has been crossed.
Password Management
Regularly change your server passwords, including administrative users and root password.
Remote Hands
Proper management of the bare metal environment includes the ability to customize it across borders without a considerable lead time.
Setting Up and Monitoring Firewalls
These are pieces of hardware or software that prohibit unwanted traffic. A user would set up firewall rules to restrict traffic by service port, destination IP address, or IP protocol. The goal is to know which ports you need to open and for what purpose.
Unfortunately, there is no one-fits-all solution. Each instance may require a unique approach to traffic management.
Operational Management
This includes a myriad of tasks, such as hardware replacement, domain name services, bare metal backup and recovery, migration of data, etc.
Make Good Use of Client Portals and APIs
Most enterprise-grade service providers offer a client portal that grants clients’ insight into their resources and an opportunity to scale easily through a portal interface or an API.
Role-based Access
If a large number of your organization’s members interact with your bare metal infrastructure, you will want to create role-based segregation of duties and permissions.
The Initial Setup of Bare Metal Servers
Identifying Requirements
First, every organization needs to be aware of how they plan on using bare metal. Consider your use case; will it be a database server, network device, or application server; do you intend to use it for dev/QA or production? Every unique use case needs different configurations, and if you don’t do your research, you certainly won’t find the right solution.
When you define your requirements, you can start thinking about the configuration.
Off the Shelf Configurations and Non-Configured Setups
There are off the shelf configurations that are created for specific workloads. Most managed service providers offer servers pre-configured for data crunching, heavy graphical processing, and for other types of specialized workloads. Even if your organization requires a particular configuration, most sales teams will help you procure the right bare metal server.
OS, Control Panels, and Database Software Options
This is one significant benefit of bare metal servers. The entire concept of ‘bare’ implies a clean slate, meaning that you can use the server’s full potential. You pick the underlying relational database software (e.g., MySQL), the operating system (e.g., CentOS, Microsoft Server 2016, Ubuntu, etc.), the control panel and control panel add-ons, you have root access, and you are in full control. You have the option of doing a custom install or setting up your own hypervisor to create a virtualized environment.
All these options can be modified after your initial deployment but be aware that such modifications will require data deletion.
Other Considerations
Bare metal takes more time and know-how to implement than cloud hosting. It can also be less flexible when expanding.
Since you are tied to the hardware, any problems can have a huge impact. Cloud-based solutions circumvent this by not linking the server instance to a single physical machine.
Compared to cloud hosting, dedicated servers are most cost-effective when you are using its resources to their fullest. However, the benefits are often beyond the needs of businesses. Therefore, it is typically best to opt for a cloud server.
To Lease or Buy
Buy
The decision to lease or buy all comes down to your needs and requirements. Purchasing a server provides maximum access to hardware, but that comes at a price. Even if you set aside the necessary and often substantial upfront investments, there are also ongoing server maintenance and administration costs to consider.
It would be best if you considered the Total Cost of Ownership (TCO). TCO includes your initial investments and all operational expenses, such as system uptime, technical support, and redundancy.
If you decide to buy, plan whether you will run things on-premise or lease racks at a colocation center, which set up rooms created primarily to house servers. On-premise will strain your budget as you will need to achieve and maintain data center-like conditions.
On the other hand, private colocation grants you all the interconnectivity, redundancy, cooling, electrical power and stringent security regulations of a data center, while at the same time placing the hardware in your hands. For example, phoenixNAP’s flagship data center in Phoenix, Arizona offers you 30+ unique carrier service providers, including direct access to Amazon’s cloud service and up to 500 watts/sq. Ft. of power capacity.
Generally, colocation is a sensible proposition only if you are looking into expensive high-end servers or are in the market for several bare metal servers.
Lease
By now, you might have noticed that leasing a bare metal server is the most straightforward and most convenient option for most deployments. Ensuring the right conditions and scaling bare metal servers in-house is very vexing. That is why even some large organizations choose to lease as a simple and cost-effective alternative.
Many providers offer fast deployment and high network uptime. For example, phoenixNAP deploys your server within four (4) hours if the order doesn’t come with special instructions, and offers 100% uptime. If a component fails, onsite staff will handle troubleshooting and resolve the issue on your behalf. However, you do need to monitor for hardware fails and submit a support ticket (trouble ticket) proactively.
Server Location
The next step would be to select the server location. In today’s fast-paced environment, delivering the speediest result is crucial. Google’s DoubleClick conducted a study in 2016 on how slow loading times impact businesses. They reported that “53% of mobile site visits are abandoned if pages take longer than 3 seconds to load.” Response time has a lot to do with location and, typically, you want to avoid data passing through multiple processing points before service delivery.
Regardless of whether you lease or opt to physically place your servers in a colocation center, carefully pick the right service provider. Start by identifying your users’ geographical location. If you are running a global business, the right thing to do would be to find a global provider with multiple presence points.
On-Premise
The alternative here is to buy and physically control the server on company property. This is known as an on-premise setup. However, servers require particular conditions to maintain proper function. Temperature, humidity, proximity to automated cooling, and the server’s physical safety are among the most important considerations.
Additionally, security is of paramount importance. Some industries, such as healthcare and payment processing, prescribe very stringent security rules (i.e., HIPAA and PCI).
Organizations processing delicate information must adhere to these rules, and failing to do so might come at a steep price if a consumer data breach affects their systems or infrastructure. This makes an on-premise setup very complicated and time-consuming. Quality IT service providers maintain PCI-DSS and HIPAA Compliance, thus providing a secure platform for your business.
No organization should install bare metal servers on-premise if they aren’t 100% sure to maintain the proper environmental conditions, maintain efficient redundancy, and adhere to security protocols.
For the sake of simplicity, we will consider the only colocation and leasing bare metal servers for the remainder of this article.
Public Bandwidth
How much traffic are you expecting? Most managed service providers offer somewhere in the range of 15 TB of free public bandwidth monthly. If you predict higher traffic volumes, be sure to upgrade your service plan. Good service providers may offer up to 250 TB of bandwidth at 550Gbps+ capacity to minimize network latency.
RAID Setup
Hard disc drive failure (HDD) is the most common issue you will encounter in your server setup. Moreover, if you opt for a managed service, meaning that it’s not your task to replace the hard disk drive, you certainly wouldn’t want to lose precious data.
A redundant array of independent disks (RAID) is a redundant system that uses multiple hard drives to store your data. This means that data is written to all drives in the array, allowing for a hard drive to fail without losing data. RAID is used for critical workloads where failure and data loss would be catastrophic and detrimental to an organization. Bear in mind that RAID’s objective is to reduce downtime, but it doesn’t eliminate the need for backups.
There are several types and levels of RAID:
RAID 0 – Data is chunked and split between drives using striping, speeding up writing and reading speeds. This setup does not offer any protection. If one hard drive fails, all data is lost. The usable capacity is equal to the total physical capacity.
RAID 1 –This setup uses a process called ‘mirroring.’ It writes data to both hard disks, so you don’t lose data even if one disk fails. Bear in mind that this halves your storage capacity. This means that if you provision 20 TB of storage space, you have 10 TB of usable capacity.
RAID 5 – Data is written across all drives (minimum of three drives) with additional information called ‘parity.’ If any hard disk fails, data can be retrieved using that extra information. The usable capacity will be the total storage less one hard drive. RAID 5 takes performance hits during a write phase, so it is not recommended for database servers.
RAID 10 –This is a combination of RAID 1 and RAID 0. Data is organized as stripes across several hard drives, and then the striped disks are mirrored. The usable capacity is 50% of the total physical capacity.
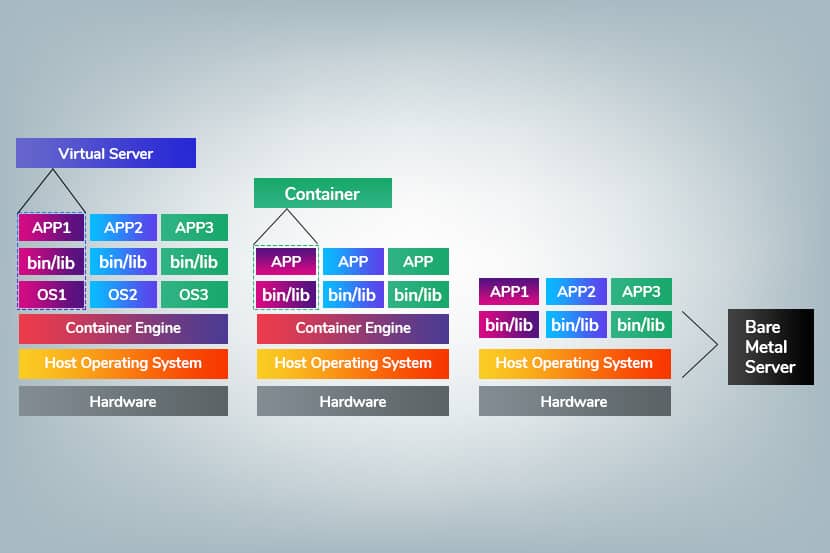
Bare Metal Environment vs. Virtualization
The virtualized environment is the primary alternative to the bare metal server.
Many differences dictate the usefulness of each environment for business.
First, let’s define virtual machines and then look at some of the most important distinctions between the two infrastructures.
When speaking of cloud instances, each virtual machine is part of a shared hosting environment with multiple tenants. For example, each tenant may have one virtual machine on a single shared physical server. In modern deployments, however, virtualized environments can also be dedicated, meaning that there is segregation of hardware.
For example, Private Cloud hosting is one example of a highly customizable single-tenant cloud service.
Generally, VMs are easily scalable and budget-friendly but lack the computing power of bare metal servers.
Performance
A bare metal server outpaces virtual machines in performance, all else being equal. Because there is only a single tenant on a dedicated server, that tenant has access to all the physical resources without having to share. A virtual server may separate clients, but those clients share optimized resources on the same physical server.
The presence of a hypervisor prohibits software that can take advantage of architectural perks of the physical hardware. This places bare metal users in a unique position to make far better use of specific hardware pieces.
Security
Compared to public cloud instances, server colocation and bare metal servers have heightened security because of their isolation away from other clients. In the world of multi-tenant virtualized servers, data streams infected by malware may affect the distribution of resources across the server. Although other data streams are quarantined from the infection, the neighbors may suffer the effects of a redirected resource load.
Resource Usage
Resource usage on bare metal servers is highly predictable compared to virtualized environments. If you plan on crunching data or running apps with unexpected usage spikes, getting a bare metal server is your best bet. Crunching data in the cloud will most certainly get very expensive as you would have to provision vast capacities to maintain predictable performance.
Control
A single tenant exercises more control over a single physical server than a group of people does in the cloud. The bare metal environment allows a client to fully control and predict bandwidth, memory usage, and other important web hosting aspects.
Scaling
Virtual machines are far easier to scale as additional resources can be provisioned in a couple of minutes. This means that with bare metal servers, you need to plan. It is more challenging to scale and adapt to current requirements.
Another thing to consider is that a single VM doesn’t offer enough resources for some use cases. For example, a single VM may be limited to 64 GB RAM, 2 TB of storage, and 8 vCPU. In contrast, a bare metal solution may offer the maximum resource limit of the latest technology.
Long-Term Hosting Solution
Virtual machines are often deployed for short-term use, while bare metal is considered one of the favored solutions for long-term deployments. There are several significant contributing factors.
First, there are no other tenants to compete with for the server’s physical resources, so it is much easier to scale and combine your resources. Even though many service providers don’t place a hard limit on virtual resources, there is a soft limit in place.
Secondly, an organization’s requirements are bound to evolve. The additional customization options bare metal servers feature means that bare metal servers can cater for a wide range of workloads. Furthermore, bare metal can be an excellent starting point for a hybrid environment. A hybrid environment combines bare metal servers and modern cloud solutions to provide the best of both worlds.
Industries with compliance guidelines can make use of dedicated servers for increased security. The sectors of healthcare, finance, and the government should have the financial and personal data of end users stored in compliant infrastructure. Colocation is a good fit for these use cases.
Hybrid: The Best of Both Worlds
It is possible to capture the best of both worlds by bringing together bare metal and virtualization. In this model, each tenant is not tied to a specific physical machine but still has the power and access of a dedicated server. Each physical server has a single virtual tenant running on it.
With a hybrid setup, businesses can run their most demanding workloads while also enjoying cloud hosting’s flexible structure. Users provision and manage servers using a web-based portal. So, the time and cost of configuration can be close to those of services hosting in a shared, virtual environment. This also makes it easy to upgrade servers when needed.
Learn more what is bare metal cloud and the best use cases for the technology are. For more details, visit our Bare Metal Cloud provider service page.
When It’s the Right Choice
Specific workloads suit a bare metal set up better than others. Businesses that have high performance and/or security needs may get a lot out of this option.
Dedicated machines are great for workloads that require a lot of computing resources and low latency. Some examples of this include streaming video, hosting large amounts of graphics, or running taxing web apps. Teams who are rendering animations or working with large amounts of data can also get a lot of mileage from bare metal.
Businesses that deal with compliance or have data that needs to be kept very secure may also prefer to use bare metal. For example, teams that are in the healthcare or finance space are great fits for this offering. It is easier to control access to a dedicated server. Also, the hardware can be set up to meet regulatory requirements.
Are Bare Metal Servers a Good Fit?
Bare metal servers continue to be an essential component of many companies IT infrastructures. There are many advantages to using this environment.
Bare metal offers the best that current technology has to offer. When hosting bare metal with an Infrastructure-as-a-Service provider, you can quickly scale globally by leveraging the provider’s expertise across all professional dimensions of managing such infrastructure. This means that you get an affordable way to cluster your resources, globally.
Other perks of bare metal include the ability to hybridize your infrastructure by unifying your bare metal and virtual assets.
Growing businesses should consider bare metal as a long-term solution for data storage and transfer. There is no better solution when it comes to pure power, the flexibility of structure and customization capabilities.