Top eCommerce Security Threats with Solutions
Ecommerce security isn’t something to be taken lightly. Major data leaks have fundamentally damaged trust in digital security. Consumers are comfortable making payments through familiar systems (PayPal, Amazon, Google, Apple, etc.) but take a bit more convincing to risk their credit card details with unknown companies. After all, they know what’s at stake.
Failing to secure an online retail business can directly impact sales or worse, ruin your reputation. Once it’s known that a business cannot be relied upon to keep data secure, no one will want to buy from them again.
Get serious about protecting your online business. Learn the basics of what you need to know about eCommerce security threats and solutions.
Major Threat: Transaction fraud
Vast amounts of money change hands online with each passing second, and as much as we’d like to think that technology has moved past transactions being dangerous to consumers, it hasn’t. There are two primary forms of payment fraud. The first is stolen credit cards, whose details are used to make unauthorized payments (with the purchased products kept or sold on, even if the payments get canceled). The second is transactions on insecure systems that are interrupted or get redirected.
Online buyers now have access to systems offering unprecedented financial convenience. Bank support is available through live chat, and you can even cancel payments through apps. But this doesn’t fully protect from this type of fraud. The reason is simple: even the most diligent among us will forget to check our bank records on occasion, and it only takes one lapse in attention for a cybercriminal to make numerous payments.
Online shoppers are now aware of the importance of website security markers, such as the HTTPS indicator. Still, such indicators can often be spoofed in a manner that’s sufficiently convincing for most people. This type of forgery can make it quite tricky to tell when a website is providing a secure service. Consumers need to be educated and get better at being vigilant online.
Solution: PCI DSS compliance
The PCI DSS standard was set up to raise levels of online payment security dramatically. Any eCommerce business that wants to protect its transactions (and bolster its credibility in the process) should take action to meet it. Compliance is still nowhere near as common as it should be. It’s frustrating, as it shouldn’t be an issue for the individual retailer since essentially, it’s a benefit. Compliant sellers stand out more through ridding their sales funnels of damaging dead ends (a key conversion optimization tactic) and showing their investment in buyer safety.
Major Threat: Direct site attacks
While phishing is a passive approach, eCommerce sites can sometimes be subjected to direct attacks in the form of DDoS (dedicated denial of service) campaigns. Here’s how it works: those who want to put a store under siege will program many internet-capable devices to near-constantly attempt to use the store site.
This orchestrated attack will overwhelm the store’s hosting and prevent the site from loading for most (if not all) regular visitors. It’s mainly about keeping it so busy that it can’t focus on the visits that actually matter. This attack type can also burn through hosting data allowances, causing other costly issues for businesses. These campaigns are relatively rare, but not so much so that they’re not a threat.
What’s the end goal of a DDoS attack? It depends on the situation. Sometimes it will be to inconvenience the store and damage its reputation, as a matter of corporate sabotage. More often, a DDoS attack will be coupled with a blackmail demand: pay a certain sum, and the attack will be disabled.
Solution: Active protection
An eStore can be attacked at any time, regardless of its fundamental level of security, this threat requires more vigorous measures, so make use of a DoS protection service. The concept is simple enough – incoming traffic is monitored and parsed, and when visit requests are considered to be fraudulent in nature, they are entirely blocked. This defense prevents the DDoS attack from slowing the site down to a crawl, or significantly affecting its performance.
Major Threat: Password assault
Password strategy has been frustrating security consultants since the very beginnings of the internet, all due to the irritating balance needed between protection and convenience. If you choose long and complex passwords, you can end up forgetting them and losing all access. Creating easy-to-remember passwords leaves systems highly vulnerable and open to attack.
There are two main methods for this type of attack to occur. The first is brute forcing, using a program to run through thousands upon thousands of passwords in the hope of eventually getting it right. And second, what can reasonably be called informed guessing: using pieces of information from a user’s life, gleaned off social media to identify the words most likely to appear in their passwords.
And if a key admin password is discovered, the resulting access can prove massively damaging because it might not be noticed for some time. Significant alterations can be made, systems can be taken offline, data can be stolen, and money can be transferred, all with minimal risk to the person with access. It’s like breaking into someone’s house by picking the lock – there’s no apparent damage, but it happens when you’re supposed to be home.
Solution: Stronger passwords and multi-factor authentication
How do eCommerce sellers address the threat of discovered passwords, both for their internal systems and their customers?
There are two strategies they can implement. Firstly, they should use and require that more complex passwords are used internally. They don’t need to be comically long or awkward, but they mustn’t be as simple as “1234” or “password”.
Secondly, they should start using multi-factor authentication for their admin accesses (or for major changes to customer accounts). This setup requires the logged-in user to couple their password access with another form of authentication, such as an authentication code sent via text message. It’s also worth creating regular site backups: that way, in the unlikely event, that someone does gain unauthorized access and makes sweeping changes, they can quickly revert to prior backups.
Major Threat: Social engineering
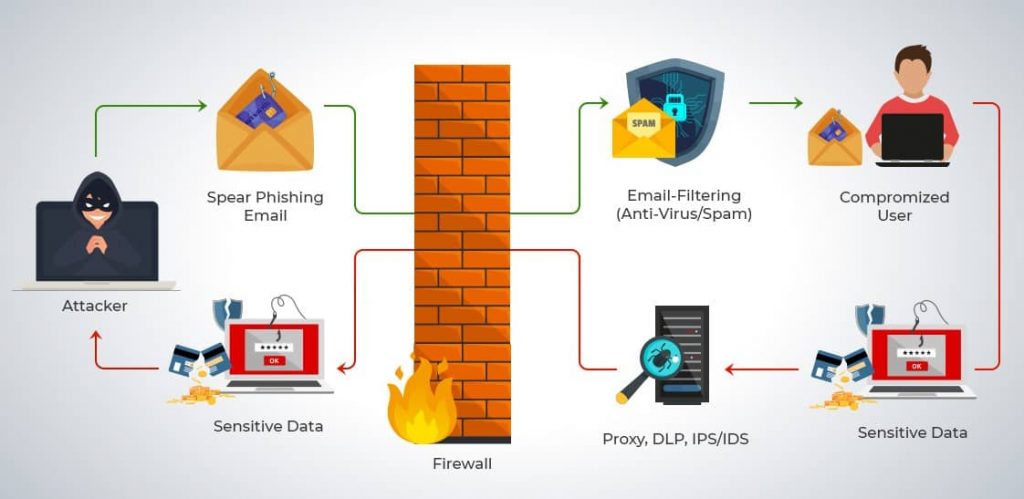
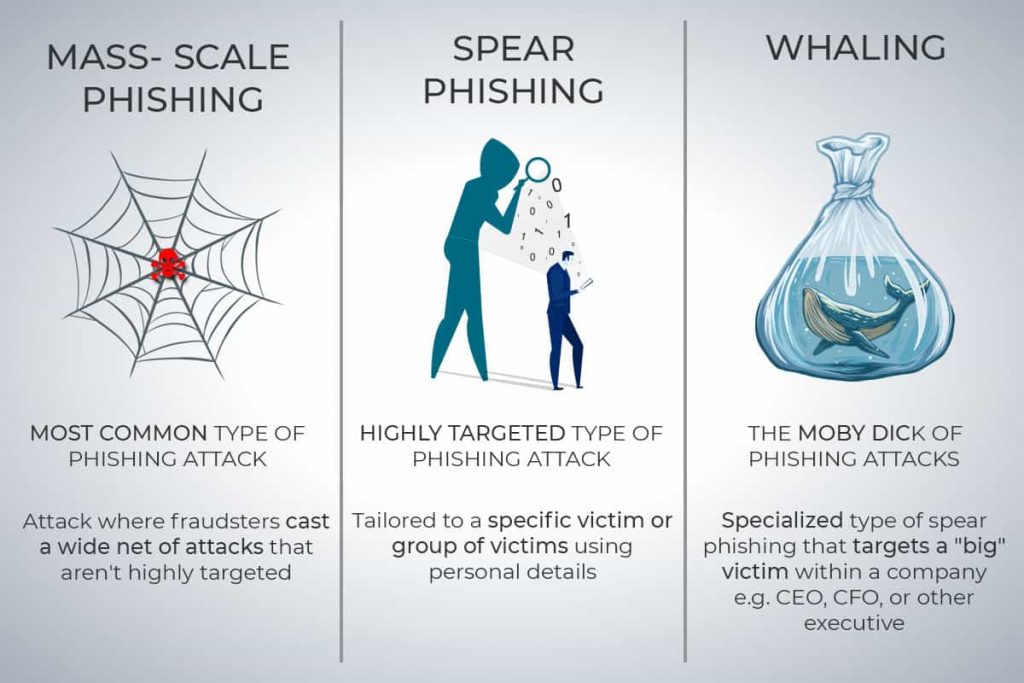
Social engineering is a broad method for gaining access to systems, money, or assets through deception at a social level instead of directly through technology. One of the most common forms of social engineering is phishing, which involves pretending to be someone trustworthy when contacting someone and exploiting that trust to get something from them.
In the recent past, phishing most commonly occurred through phone calls, letters, and even house visits. An example of a phishing attack is calling someone and claiming to be from their bank saying they need to confirm credit card details. When online shopping and eCommerce developed and became more popular, it grew more sophisticated.
At this point, phishers can learn about which retailers a shopper uses, and spoof emails from them. Emails that are loaded with risks such as fraudulent forms to keylogger installers. They can also pose as retailers through social media or set up stores that appear very similar to legitimate sites by using slightly-different URLs and steal data. These cybercriminals often use misspellings and build a store that copies the design of a trusted retailer, i.e., copying Amazon’s design and making it live at www.amazom.com.
Solution: Wider education
Phishing is difficult to prevent because it’s such a broad category, and it involves no force. It comes down to the criminals laying down the bait and hoping that people will take it. The best way to proceed is for retailers to educate their customers about how they operate. They should add tips to their site content and use their general marketing materials. Customers should know that when they receive emails, they know how to identify them as legit. Clients need to know what they might be asked for and what will never be asked of them. Retailers need to encourage their customers to reach out for confirmation if they ever receive questionable emails.
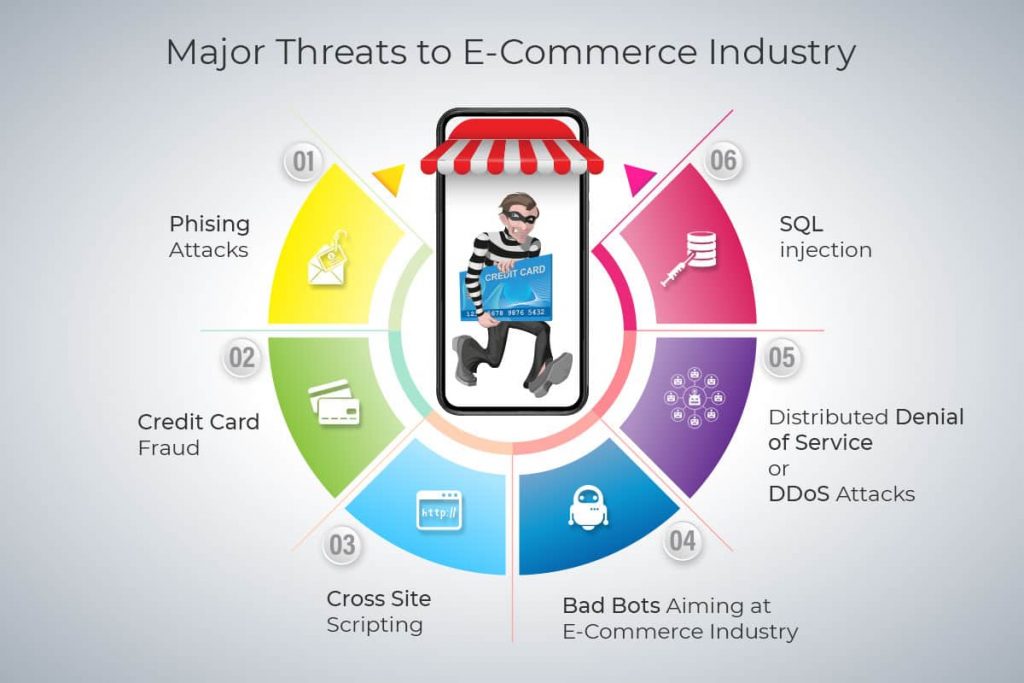
Other eCommerce Threats You Should Know
For eCommerce businesses dealing in daily monetary transactions, security must become the number one concern. Intensive security measures need to be implemented to obstruct threats effectively and keep transactions protected. Here are other common threats eCommerce sites face:
Brute Force Attacks
Brute force attacks target an online store’s admin panel. Why? They want to figure out the password and gain access, the directness of the attack makes it brute-force. After using software to connect to a site, it using code-crunching programs to crack passwords by using every possible combination imaginable. The solution is easy, protect your system by creating strong and complex passwords, changing them regularly.
Bots
Bots can be both good and bad. The good ones are those that crawl the Internet and determine how to rank your site in search engines. Bots can also scrape websites too for inventory information and pricing and alter prices on a site, freeze popular items in shopping carts, and thereby damage site sales and revenues.
The solution is to protect exposed APIs and mobile apps, and examine traffic sources regularly looking for spikes, and then blocking those hosting providers and proxy services.
Malware
There are different types of malware that want to penetrate the backend to steal sensitive site data and customer information.
Malware are those that use malvertising, ransomware, cross-site scripting, SQL injections, targeting credit card info and personal data. Malicious JavaScript coding is the most common. WordPress sites using WooCommerce and Shopify regularly get targeted by malware injections via widgets and plugin upgrades. The solution is to use professional antivirus and anti-malware software, switch to HTTPS, secure servers and admin panels and use SSL certificates while using employing multi-layer security.
Phishing
Receiving fake “you must take action” emails, either to your company or customers is a widely-used ploy and form of trickery used by hackers. It does require follow-through and unintentionally offering up login information or personal identification information. The solution here is employee training and educating consumers.
Spam
Contact forms and text boxes for blog comments are wide open to spammers. They can leave infected links that others can click on, ruining your reputation and site security. Also known as SQL injections, these cyber-attacks want to access databases via query forms. These links quietly wait for employees in inboxes and can affect site speed also. The solution is employee training and downloading spam filtering tools and anti-virus software, updating it regularly.
eCommerce Security Best Practices
Now that you’re familiar with eCommerce security concerns, and how costly they can be to the bottom line and reputation. Let’s look at solutions to help put a threat protection strategy into action.
PCI Compliance
PCI Security Standards Council releases a strict set of guidelines on how to secure an eCommerce website. It outlines which type of web hosting should be used, the level of security needed at the payment processing level, etc., Adopt their guidelines to ensure your site stays safe.
CDN
Content delivery networks (CDNs) are another layer of hosting for an eCommerce website. They improve processes by storing content on servers situated across the country in data centers knows as ‘points of presence.’ These data centers have their own security, meaning it adds another layer of security.
Security Plugins
Security plugins are important for maintaining WordPress sites, ensuring the safe installation of plugins, and keeps the front-end of a site safe. They defend sites DDoS attacks, malware, and hacking, keeping you informed when threats are detected in real-time.
Back up Data
Always back up data and do this regularly. A backup and restore plugin will help. Despite investing in many levels of security, no eCommerce site is impenetrable. Hackers have the patience and time to find new ways of cracking through a site. It’s critical to back up data so a business can recover quickly if an attack happens.
Server Security
Be sure to use a well-established ecommerce web hosting company you can trust and has top-level security features. That should include a server-side firewall, CDN, or SSL certificates and dedicated hosting plans where share server environments are not shared with other sites. Make sure they follow server security best practices.
Payment Gateway Security
Just as critical as web hosting, it’s also key to make sure that the payment gateway provider takes security very seriously and ensure all third-party websites connected to yours, prioritizes security.
Antivirus and Anti-malware Software
Always upkeep and update the network’s servers and equipment with antivirus and anti-malware software.
Firewall
The web host should have a firewall for servers, but it’s also good to have one specifically for your website and computer too. There are many security plugins that come with built-in firewalls.
SSL Certificate
ECommerce sites must have an SSL certificate as it’s the Google standard. But it’s free, and quite a simple way to add more layers of encryption and security to onsite transactions.
Update Software Regularly
Software only works so well as its latest version, so if it’s not updated when suggested by the provider, your eCommerce site and business is put at risk. Schedule updates and keep all programs, software, and plugins updated regularly.

Ecommerce Security: Plan Ahead to Stay Safe
The major threats to eCommerce security that we’ve looked at are potentially devastating not only for retailers but customers as well. For this reason, the appropriate measures must be taken, and strategies put into place to address them. You simply can’t afford to be casual about the protection of websites or customer data.
The goal should be to provide a safe place for consumers online. By protecting them, you protect the bottom line as well. Outside of the eCommerce security threats and solutions we have outlined here, do regular site security audits to stay ahead of the dangers.
Get into the habit of offering sensible security advice to your visitors. Invest in meeting the PCI DSS standard to safeguard transactions. Set up high-quality active site protection to ward off DDoS campaigns. And lastly, get into the habit of using high-quality passwords, and configure multi-factor authentication to prevent the entire site from being compromised as the result of a critical password being left on an office post-it note.